Comparing Security: Encrypt-Then-MAC vs. MAC-Then-Encrypt
What is Authenticated Encryption
Authenticated encryption is a cryptographic technique that combines both data encryption and message authentication into a single operation. It ensures not only the confidentiality of data but also its integrity, effectively protecting against unauthorized access and tampering. By incorporating encryption and message authentication codes (MACs) together, authenticated encryption guarantees that not only is the information kept secret from unauthorized parties, but any modifications or alterations to the data can be detected, preventing malicious manipulation. This approach is particularly vital in scenarios where both data privacy and trustworthiness are paramount, providing a comprehensive solution to safeguarding sensitive information in a single step.
In the realm of cryptography, ensuring data confidentiality and integrity are paramount. Two common strategies for achieving these goals are “Encrypt-Then-MAC” (ETM) and “MAC-Then-Encrypt” (MTE). These approaches involve a combination of encryption and message authentication codes (MACs) to protect data from unauthorized access and tampering. In this article, we will delve into the differences between ETM and MTE, and provide recommendations on which approach might be more suitable for different scenarios.
Encrypt-Then-MAC (ETM)
What is Encrypt-Then-MAC (ETM) and How it Works
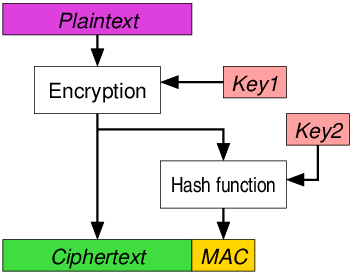
The Encrypt-Then-MAC approach follows a straightforward sequence: first, the plaintext is encrypted using a strong encryption algorithm, and then a MAC is generated from the encrypted ciphertext. This ensures that the data is both confidential and authenticated.
Advantages of ETM
Strong Integrity Protection: Since the MAC is generated from the encrypted data, any modification of the ciphertext will result in an invalid MAC when decrypted. This provides a robust defense against tampering.
Unpredictability: The attacker cannot learn anything about the plaintext by observing MACs, as they are generated from encrypted data.
In November 2014, TLS and DTLS extension for EtM has been published as RFC 7366.
MAC-Then-Encrypt (MTE)
What is MAC-Then-Encrypt (MTE) and How it Works
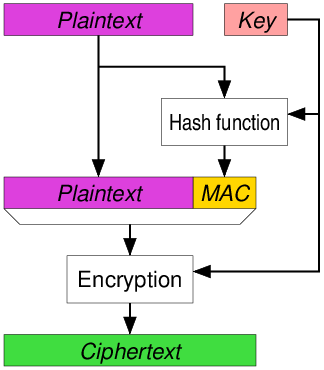
The MAC-Then-Encrypt approach takes a different route: first, a MAC is generated from the plaintext, then the plaintext and MAC are encrypted together. This method aims to protect the integrity of the plaintext before focusing on its confidentiality.
Advantages of MTE
Immediate Integrity Check: Since the MAC is generated before encryption, any modification to the plaintext will be detected during the MAC verification step, preventing the decryption of tampered data.
Reduced Padding Vulnerabilities: By MACing the plaintext before encryption, padding oracle attacks (which are tied to encryption) are mitigated.
Concerns with MTE
- Exposure to MAC-Forge Attacks: If an attacker can generate valid MACs for arbitrary data, they might be able to manipulate the encrypted content, leading to potential security vulnerabilities.
Recommendations
As TLS and DTLS use a MAC-then-encrypt construction that was regarded as secure at the time the original Secure Socket Layer (SSL) protocol was specified in the mid-1990s, but that is no longer regarded as secure.
encrypt-then-MAC, an improved security mechanism to replace MAC-then-encrypt. Encrypt-then-MAC is regarded as more secure than MAC-then-encrypt and should mitigate or eliminate a number of attacks on MAC-then-encrypt.
See also: